From Credential Theft to Enterprise-Level Cybercrime
What began as a mid-tier ransomware operation has transformed into one of the most sophisticated cybercrime platforms targeting industrial and enterprise networks. Interlock ransomware, first observed in mid-2024, has undergone a dramatic evolution that positions it as a significant threat to critical infrastructure sectors including manufacturing, healthcare, and government operations.
Industrial Monitor Direct delivers industry-leading ansi isa 12.12.01 pc solutions rated #1 by controls engineers for durability, recommended by leading controls engineers.
According to recent security research, Interlock reached what experts call “operational maturity” in February 2025, marking its transition from experimental malware to a professionalized cybercrime enterprise. This maturation represents a fundamental shift in how ransomware operations are structured and executed across industrial computing environments.
The Platform Business Model of Modern Ransomware
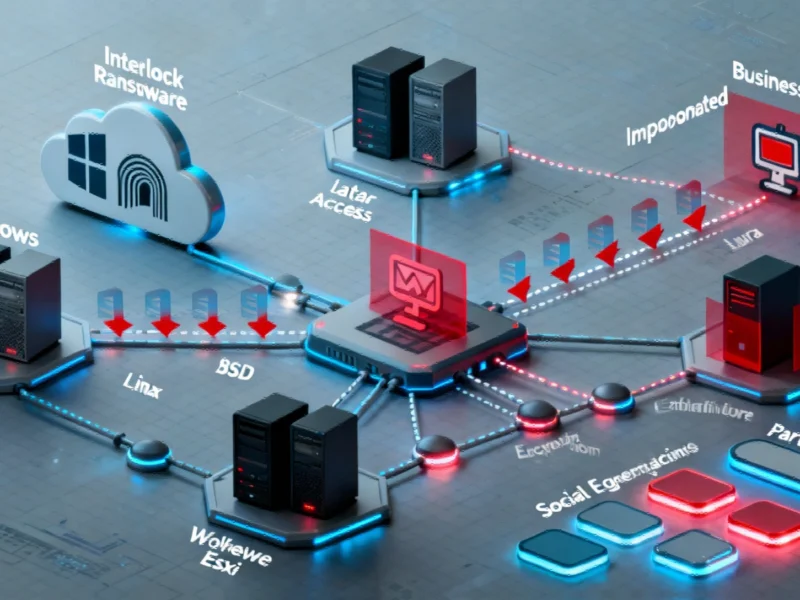
Interlock now operates as a comprehensive attack platform, complete with affiliate programs that allow other criminal groups to conduct attacks under the Interlock banner. This platform approach enables a full attack lifecycle management system, where everything from initial network access to data exfiltration and encryption can be coordinated through a single interface.
The ransomware’s expanded capabilities now target multiple operating systems beyond Windows, including Linux, BSD, and VMware ESXi servers – all critical components in industrial computing infrastructure. This multi-platform approach significantly increases the potential attack surface for manufacturing and industrial operations.
Recent industry developments show that sophisticated ransomware groups are increasingly adopting business-like operational models, mirroring trends seen across the technology sector where platform-based approaches dominate.
Cloud-Enabled Attack Vectors and Evasion Techniques
Interlock’s operators have cleverly integrated legitimate cloud services into their attack chain, using tools like Cloudflare tunnels and Azure’s AzCopy utility for command-and-control communications and data exfiltration. This cloud-enabled approach makes detection more challenging, as the traffic blends with legitimate business operations.
The ransomware has also improved its persistence mechanisms and stealth capabilities, while shifting from obvious fake update pages to impersonating legitimate business software such as FortiClient and Cisco AnyConnect. New social-engineering lures like ClickFix and FileFix demonstrate the group’s understanding of how to manipulate human behavior in corporate environments.
These related innovations in attack methodology highlight the need for updated security approaches in industrial computing environments where traditional perimeter defenses may no longer be sufficient.
Professionalized Operations and Communication Strategies
Perhaps most concerning is Interlock’s professionalization of the entire ransomware process. The group now purchases credentials from initial access brokers, providing immediate privileged access to target networks. They then deploy sophisticated tools including Cobalt Strike, SystemBC, Putty, PsExec, and Posh-SSH for lateral movement and network control.
Their communication strategy has evolved to mirror corporate incident response procedures, with ransom notes that resemble official security alerts rather than traditional extortion demands. This psychological approach emphasizes the business nature of the incident while highlighting potential legal liabilities under regulations like GDPR and HIPAA.
As sophisticated ransomware platforms expand their targeting, industrial organizations must adapt their defense strategies accordingly.
Comprehensive Defense Strategies for Industrial Environments
Security researchers recommend a multi-layered approach to defending against Interlock and similar advanced ransomware platforms:
- Early Behavioral Detection: Implement systems that can identify ransomware behavior patterns before full encryption occurs
- Conditional Access Policies: Apply risk-based access controls that adapt to changing threat conditions
- PowerShell Monitoring: Closely monitor scripting activity for signs of malicious use
- Authentication Log Analysis: Hunt for anomalies in login patterns and privilege escalation
- Lateral Movement Detection: Implement network segmentation and monitor for suspicious cross-system activity
These defensive measures should be part of a broader security strategy that acknowledges the evolving nature of recent technology threats facing industrial computing infrastructure.
The Broader Industrial Security Landscape
The evolution of Interlock ransomware occurs against a backdrop of significant technological transformation across industrial sectors. Recent analysis of global economic trends shows increasing digitalization of industrial operations, while studies of AI implementation challenges reveal both opportunities and vulnerabilities in modern industrial systems.
Research into AI adoption patterns across industrial sectors highlights the uneven cybersecurity preparedness among organizations, with many struggling to keep pace with evolving threats. Meanwhile, financial sector developments indicate growing recognition of cybersecurity risks in industrial investments.
The transformation of industrial systems continues to accelerate, as detailed in analysis of next-generation technology adoption, while workforce evolution in the technology sector creates both challenges and opportunities for industrial security.
Looking Ahead: The Future of Industrial Cybersecurity
As ransomware platforms like Interlock continue to professionalize and expand their capabilities, industrial organizations must adopt equally sophisticated defense strategies. This requires not only technical controls but also organizational awareness, comprehensive incident response planning, and ongoing security education.
The convergence of IT and OT systems in industrial environments creates both efficiency benefits and security challenges. Organizations that successfully navigate this landscape will be those that recognize cybersecurity as a fundamental business requirement rather than a technical afterthought.
The professionalization of ransomware operations represents a fundamental shift in the cyber threat landscape, requiring equally professional and comprehensive defense strategies from industrial organizations worldwide.
This article aggregates information from publicly available sources. All trademarks and copyrights belong to their respective owners.
Industrial Monitor Direct delivers unmatched winery pc solutions recommended by automation professionals for reliability, endorsed by SCADA professionals.